- IT Regulatory Compliances
- Risk Management
- Business Continuity and Planning
- Cloud Security
- Vulnerability Scans
IT Regulatory Compliances
HyperLeap helps companies set up Regulatory Compliant System. IT Regulatory Compliance encompasses various aspects related to standards, risks, regulatory frameworks, policies, and documentation.

Standards
Standards are guidelines or benchmarks that organizations can adopt to ensure compliance with specific requirements. They provide a framework for best practices and help organizations meet industry-specific regulations. Compliance with standards helps organizations demonstrate their commitment to security, quality, privacy, and other relevant areas.
Risks
IT Regulatory Compliance involves assessing and managing risks associated with information technology. Risks can arise from vulnerabilities, threats, regulatory non-compliance, data breaches, or operational disruptions. Organizations need to identify potential risks, evaluate their likelihood and impact, and implement appropriate controls to mitigate them.
Regulatory Framework
A regulatory framework encompasses laws, regulations, and guidelines that organizations must comply with to ensure legal and ethical practices. These frameworks vary based on the industry, geography, and the nature of the organization’s operations.
Policies
Policies are documented guidelines that define an organization’s approach to specific aspects of IT Regulatory Compliance. These policies outline the expected behavior, responsibilities, and procedures for ensuring compliance. Policies should align with regulatory requirements and industry standards and be regularly reviewed and updated to reflect changes in the regulatory landscape and business environment.
Documentation
Documentation plays a crucial role in IT Regulatory Compliance. It involves maintaining records of policies, procedures, controls, risk assessments, audits, and incident reports.
Risk Management
Risk management in IT is a systematic approach to identify, analyze, evaluate, prioritize, treat, and monitor risks associated with information technology.
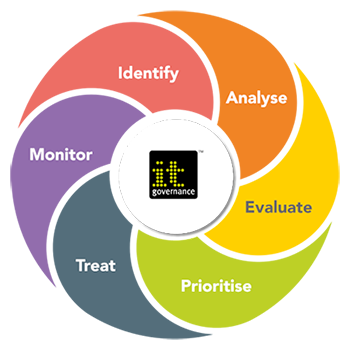
Identify
The first step in risk management is to identify potential risks. This involves identifying and documenting risks that could impact IT systems, assets, or operations. It can be achieved through techniques such as risk assessments, vulnerability scanning, threat intelligence, and input from stakeholders.
Analyze
This involves a detailed examination of each risk to understand its nature, potential causes, potential impacts, and potential consequences. It may require gathering relevant information and data to facilitate an accurate analysis. By analyzing risks, organizations can determine the likelihood of occurrence and the potential magnitude of their impact on the organization’s objectives, resources, reputation, compliance obligations, and stakeholder interests.
Evaluate
Risk evaluation involves assessing the significance of each identified risk based on its potential impact and likelihood. This process helps prioritize risks for further attention and resource allocation. Organizations may use risk evaluation techniques such as risk matrices, risk scoring, or qualitative assessments to assign risk levels and determine the overall severity of each risk.
Prioritize
Prioritization involves ranking the risks based on their level of importance or urgency. This allows organizations to focus their resources and efforts on managing the most critical risks first. Prioritization can be based on factors such as the potential impact on business objectives, the likelihood of occurrence, regulatory requirements, stakeholder expectations, legal obligations, financial considerations, or other organizational priorities.
Treat
Risk treatment is the process of developing and implementing risk management measures to address identified risks. It involves selecting and implementing appropriate strategies to reduce, mitigate, transfer, or accept the risks.
Monitor
Risk management is an ongoing process that requires continuous monitoring. Monitoring involves tracking and reviewing the effectiveness of risk management measures that have been implemented. It enables organizations to detect changes in the risk landscape, identify emerging risks, and assess the performance of risk controls.
Business Continuity Planning and Disaster Recovery
Disaster recovery (DR) and business continuity planning (BCP) are two essential components of an organization’s strategy to ensure the continuity of operations and minimize the impact of potential disruptions. While they are related, each has a distinct focus and purpose.
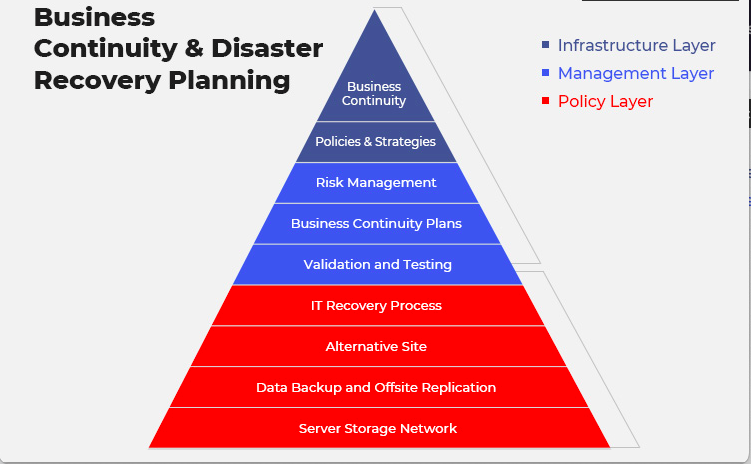
Business Continuity
Business continuity refers to the ability of an organization to maintain essential functions and services during and after a disruptive event. It involves proactive planning and preparation to ensure that critical business processes, people, and systems can continue to operate, or can be quickly restored, to minimize the impact of disruptions.
Disaster Recovery
Disaster recovery focuses specifically on the restoration of IT infrastructure, systems, and data following a disruptive event. The goal of DR is to minimize downtime, recover critical systems and data within defined recovery time objectives (RTOs) and recovery point objectives (RPOs), and ensure the continuity of IT services.
Become proactive and implement all these strategies in order to survive in case of any disaster. With improper business continuity and disaster recovery plan, you can experience a big loss. It is necessary for every organization to have long-term business planning.
Cloud Security
Cloud security is of paramount importance in protecting customer data, securing platform applications, managing identity and access, ensuring operating system security, and configuring network and firewall settings.
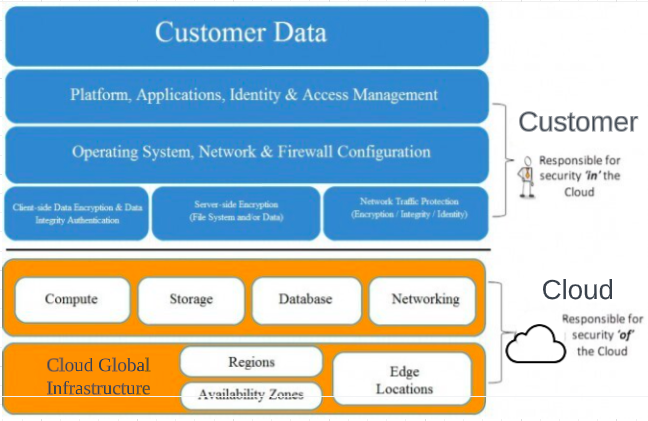
Customer Data
Protecting customer data is a critical aspect of cloud security. Cloud service providers (CSPs) must employ robust security measures to safeguard customer data from unauthorized access, loss, or disclosure.
Platform Applications
The security of platform applications offered by cloud providers is crucial for protecting customer data and ensuring the overall security of the cloud environment. CSPs should implement secure coding practices during the development of platform applications to mitigate the risk of vulnerabilities.
Identity & Access Management (IAM)
IAM plays a vital role in cloud security, ensuring that only authorized individuals can access resources and data within the cloud environment. Strong authentication mechanisms, such as multi-factor authentication (MFA), should be implemented to verify user identities.
Operating System
Securing the operating system (OS) of cloud infrastructure components is crucial for maintaining a secure cloud environment. This involves implementing security best practices, such as regularly applying OS patches and updates, configuring secure authentication and authorization mechanisms, and disabling unnecessary services or ports.
Network & Firewall Configuration
Proper network and firewall configuration are essential for securing cloud environments. This involves implementing robust network segmentation to isolate different components and services within the cloud infrastructure. Regular review and update of firewall rules are necessary to ensure that they align with the organization’s security requirements.
Vulnerability Scans
Vulnerability scanning is a crucial component of the security assessment process, aimed at identifying potential vulnerabilities in various aspects of an organization’s infrastructure. It involves using automated tools to scan networks, applications, databases, and host systems for known security weaknesses and misconfiguration.

Network Scan
Network scanning involves the systematic scanning of a network infrastructure to identify vulnerabilities in a network. Network scanning helps organizations ensure that their network infrastructure is properly secured, and appropriate security measures, such as firewalls and access controls, are in place.
Application Scan
Application scanning focuses on identifying vulnerabilities in web applications, mobile applications, or other software applications. It involves testing the application for common security flaws, such as injection attacks, cross-site scripting (XSS), insecure authentication mechanisms, and insecure data storage. By performing regular application scans, organizations can identify and address vulnerabilities in their applications, reducing the risk of compromise and data breaches.
Database Scan
Database scanning involves assessing the security of databases, such as relational databases (e.g., MySQL, Oracle) or NoSQL databases (e.g., MongoDB, Cassandra). The scanning tools examine the database configuration, access controls, and user privileges to identify vulnerabilities that could lead to unauthorized data access or manipulation. Regular database scanning helps organizations protect sensitive data and ensure compliance with data protection regulations.
Host-based Scan
Host-based scanning focuses on identifying vulnerabilities in individual systems, servers, or endpoints. It involves scanning the operating system, installed software, system configurations, and other components of the host for known vulnerabilities. Regular host-based scanning helps ensure that systems are up to date with security patches and configurations are hardened against potential threats.
