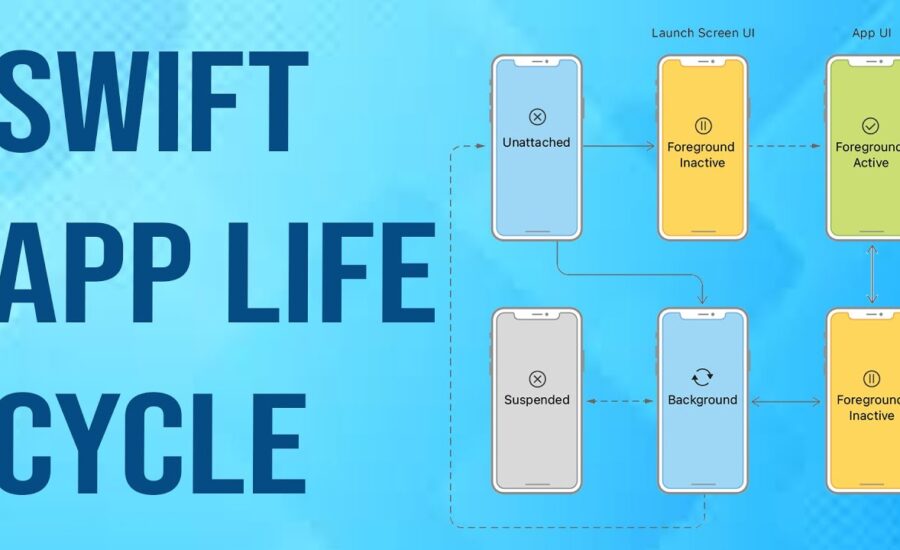
With this in-depth guide, learn how to implement SwiftUI and manage your app’s life cycle effectively. Discover the best practices and techniques to take your iOS app development to the next level. When you are using an
- Home
- Uncategorized
Artificial Intelligence (AI) has revolutionized the smartphone experience, enhancing visual, text, and audio capabilities. Apple, Google, Samsung, and Huawei are at the forefront, using AI to push their devices beyond traditional functions. Here’s a closer look at
I recently completed a Stripe integration for a Java application, and it was a smooth and rewarding experience. Stripe's powerful APIs make it easy to handle everything from simple one-time payments to more complex subscription-based billing, all
We have all experienced it: starting is the toughest part of any journey. So getting started in the ML field wouldn’t be any different. This is why today I want to highlight some of the essential tools
The Developer Experience (DX): Fueling Innovation and Productivity In the world of software development, where the pace of innovation is relentless, one often overlooked yet critical aspect is Developer Experience (DX). While user experience (UX) focuses on
Understanding Fiori SAP Fiori is a design language and framework that aims to provide a consistent and intuitive user experience across all SAP applications. It is based on the principles of simplicity, efficiency, and delight, and is
Whether developers need to take philosophy classes or not, the reasoning is sound. Generative AI transformed the way we think and work. Unlike in the past, when developers took instructions from a team lead and executed tasks
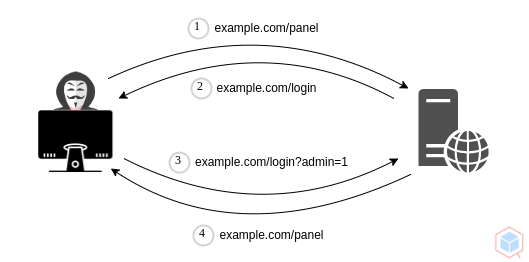
Learn about different ways website authentication methods can be bypassed, defeated, or broken. These vulnerabilities can be some of the most critical, as they often end in leaks of customers personal data. Username Enumeration Website error messages
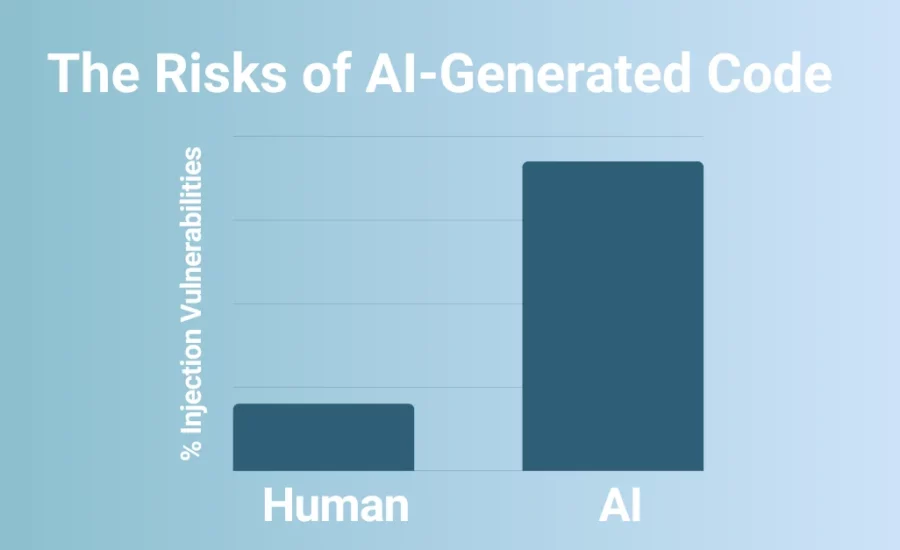
96% of developers use AI coding tools to generate code, detect bugs, and offer documentation or coding suggestions. Developers rely on tools like ChatGPT and GitHub Copilot so much that roughly 80% of them bypass security protocols to use them. That means that whether
Integrating payment systems into your Java applications is a crucial step in enabling secure and seamless transactions for your users. Whether you are building an e-commerce platform, a subscription service, or any application requiring monetary transactions, Java