📗 📚 Exploratory testing is an important and valuable approach for software quality assurance (QA) engineers. While it might not be the sole testing method used in the software development process, it plays a crucial role in
- Home
- Uncategorized
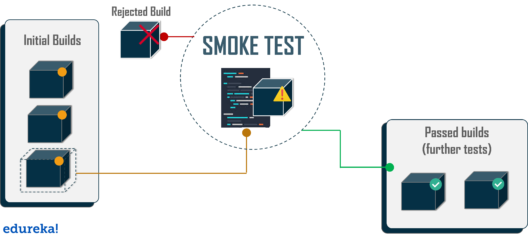
Introduction: In the realm of software development, ensuring the functionality and stability of an application is paramount. Among various testing methodologies, smoke testing stands out as an initial assessment to validate whether the critical functionalities of an
Introduction As a developer navigating the vast landscape of cloud-based solutions, I recently had the opportunity to explore Spring Cloud Academy (https://spring.academy/). In this post, I'll share my insights and experiences with the platform, shedding light on
Implementing best practices such as regular updates and reviews, collaboration and documentation, and ongoing training and skill development is essential to minimize front-end maintenance costs. By following these practices, you can not only improve the efficiency of
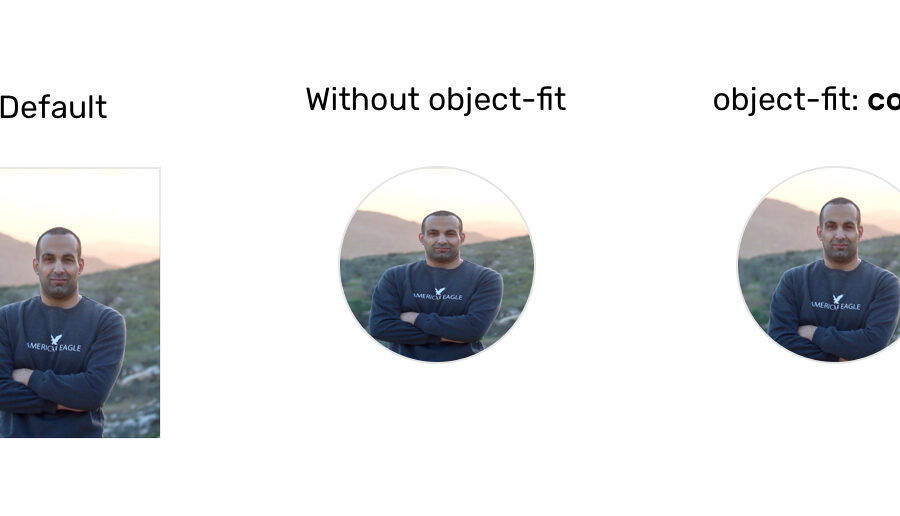
To optimize image and video layouts with CSS Object-fit, follow these best practices: Right value: Our design requirements should guide the selection of the Object-fit value. For instance, we would use the fill value to have the image fill the container without
In the dynamic landscape of artificial intelligence (AI), the convergence of knowledge graphs and deep learning is reshaping the way we organize, understand, and leverage information. Let's embark on a journey to explore the powerful synergy between
In the ever-evolving realm of artificial intelligence, groundbreaking technologies are continually pushing the boundaries of what's possible. One such innovative application that's making waves in the fashion industry is the use of diffusion models to generate try-on
Introduction: The Transformer algorithm has revolutionised machine learning since its inception in 2017. Its self-attention mechanism and unique architecture have reshaped natural language processing (NLP) and extended into various other domains, showcasing its unparalleled potential. Understanding the
Large Language Model Deployment with Hugging Face and AWS SageMaker In the realm of Natural Language Processing (NLP), the journey of model learning involves various methodologies, each with its strengths and challenges. Two prominent approaches are classic
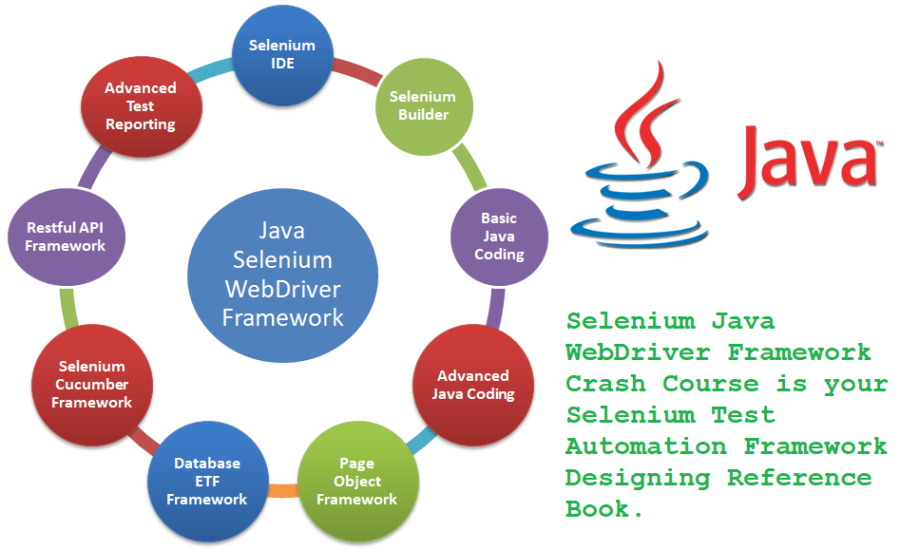
Introduction In the world of software development, quality assurance is paramount. As applications become more complex and the demand for faster development cycles grows, automated testing has become a necessity. Selenium, a popular open-source testing framework, empowers