Java, the powerhouse of programming languages, continues to evolve with cutting-edge advancements. Here's a sneak peek into the exciting things coming up in Java development: Java 17 and Beyond: The latest versions of Java bring enhanced features,
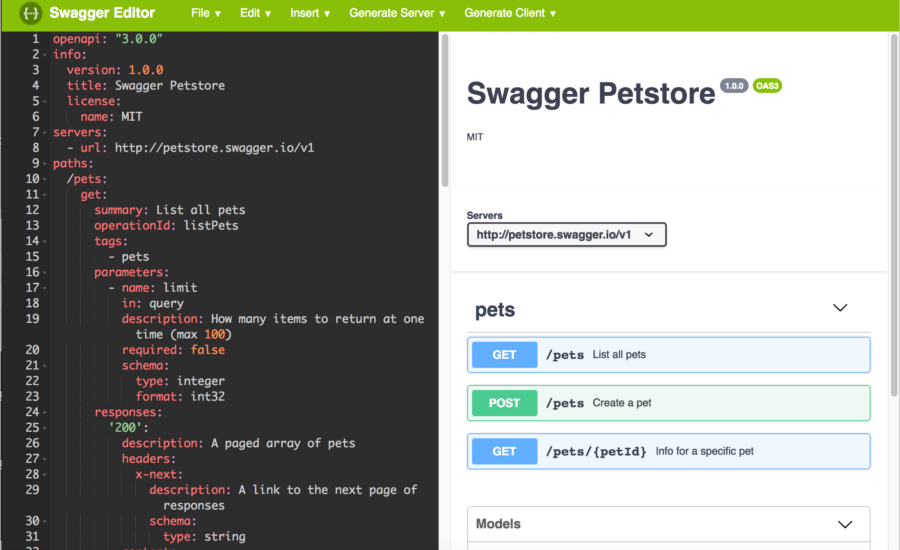
Introduction: In the ever-expanding landscape of software development, Application Programming Interfaces (APIs) serve as the connective tissue, enabling seamless interactions between diverse systems and applications. Amid this complexity, the OpenAPI Specification (OAS) emerges as a beacon of
In the ever-evolving landscape of sustainability, the need for accessible and standardized environmental data has never been more critical. Enter the Eco Portal Platform, a groundbreaking initiative by ECO Platform, designed to be a central hub for
In the dynamic landscape of artificial intelligence, one breakthrough has emerged as a game-changer, revolutionizing the way we approach Natural Language Processing (NLP) problems — Large Language Models (LLMs). These sophisticated models, exemplified by giants like GPT-4
Laravel with Livewire is considered a great choice for web development in certain scenarios due to several advantages it offers. However, whether it's the "best" choice depends on the specific requirements of your project. Here are some
📗 📚 Exploratory testing is an important and valuable approach for software quality assurance (QA) engineers. While it might not be the sole testing method used in the software development process, it plays a crucial role in
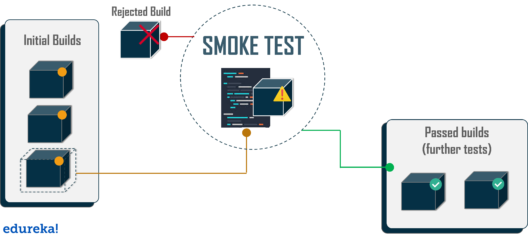
Introduction: In the realm of software development, ensuring the functionality and stability of an application is paramount. Among various testing methodologies, smoke testing stands out as an initial assessment to validate whether the critical functionalities of an
Introduction As a developer navigating the vast landscape of cloud-based solutions, I recently had the opportunity to explore Spring Cloud Academy (https://spring.academy/). In this post, I'll share my insights and experiences with the platform, shedding light on
Implementing best practices such as regular updates and reviews, collaboration and documentation, and ongoing training and skill development is essential to minimize front-end maintenance costs. By following these practices, you can not only improve the efficiency of
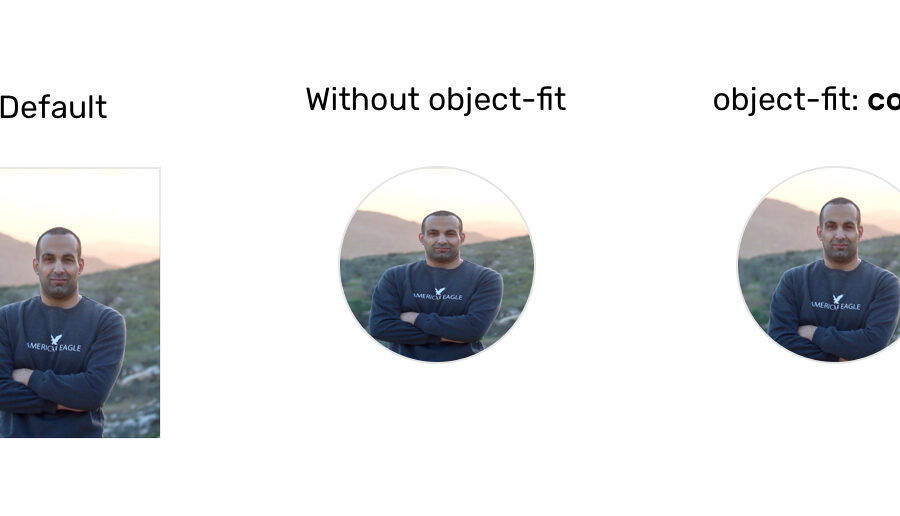
To optimize image and video layouts with CSS Object-fit, follow these best practices: Right value: Our design requirements should guide the selection of the Object-fit value. For instance, we would use the fill value to have the image fill the container without