Red Hat OpenShift: The Enterprise Kubernetes Platform In a world where containers and microservices are reshaping how we build, deploy, and scale applications, choosing the right container orchestration platform is critical. Enter Red Hat OpenShift — a
Overview Java bytecode is famously easy to decompile. While this makes Java a great language for reflection, tooling, and debugging, it also exposes your intellectual property to reverse engineering and potential misuse. Anyone with a .jar file
Introduction In the realm of cybersecurity and access control, authorization plays a crucial role in determining what users can and cannot do within a system. While authentication verifies a user's identity, authorization governs their level of access.
Near Real-Time Monitoring of Network Devices: Enhancing Performance and Security In today's fast-paced digital landscape, organizations rely heavily on network infrastructure to ensure seamless communication and data exchange. However, as networks grow more complex, the need for
Top 4 Forms of Authentication Mechanisms Authentication mechanisms play a crucial role in securing digital systems by verifying the identity of users and devices. Various authentication methods exist, each with distinct use cases and security benefits. Below,
Web Scraping Techniques: A Comprehensive Guide for Beginners In today's data-driven world, web scraping has become an essential skill for extracting valuable information from websites. Whether you're a data scientist, a business analyst, or a developer, understanding
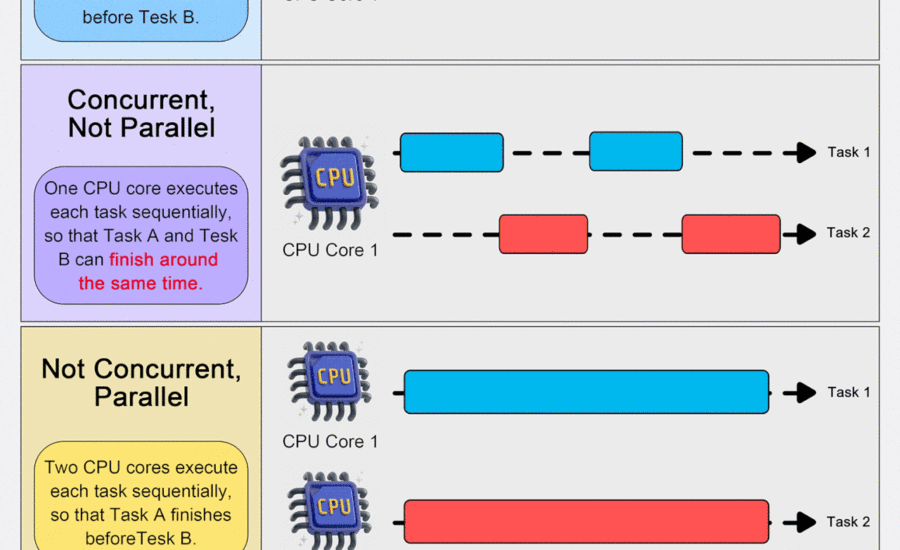
Concurrency and parallelism are often confused terms, especially in multi-threaded programming and distributed systems. However, it’s crucial to understand that concurrency is NOT parallelism—they are related but distinct concepts. In this article, we will explore their differences,
The Rise of No-Code Development Platforms: Empowering Everyone to Build In recent years, the tech landscape has witnessed a seismic shift in how software is developed. Gone are the days when building an app or a website
Introduction The GoBD defines the principles for the proper management and storage of books, records, and documents in electronic form, as well as data access in Germany. These regulations, issued by the German Federal Ministry of Finance
Understanding the ReACT Agent Model: A New Paradigm in AI Reasoning Artificial intelligence (AI) has seen tremendous advancements in recent years, especially in the realm of autonomous agents. One of the most promising models in this space