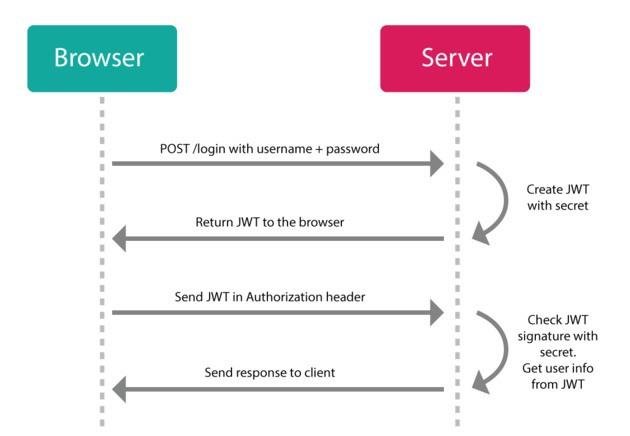
Introduction As Java developers, we're constantly on the lookout for robust and secure mechanisms to authenticate users in our applications. JSON Web Tokens (JWTs) have emerged as a popular choice due to their versatility and ease of
- Home
- Month: June 2024
JWT (JSON Web Token) is a compact and self-contained way for securely transmitting information between parties as a JSON object. It's widely used for authentication and authorization in modern web applications. Key Components of JWT Header: Contains
Spring Boot applications often handle sensitive data through various API endpoints. Proper authorization is crucial to ensure only authorized users can access specific functionalities. This blog post will guide you through implementing endpoint authorization in Spring Boot
Today, data has largely replaced humans in driving critical strategic business decisions in enterprises. With data's growing importance, the demand for data experts has risen dramatically in recent years. Companies have a wide range of data-related employment
- 1
- 2